Introduction
As we progress further into a digital-first landscape, application security has transitioned from being optional to a fundamental business necessity. Whether you are developing an e-commerce site, a mobile banking application, or a straightforward booking system, safeguarding user information will influence your reputation and long-term viability.
As cyber threats grow increasingly sophisticated each year, being knowledgeable about the optimal security practices for 2026 can enable you to mitigate risks and provide a more secure experience for your clients. This is one of the primary reasons many entrepreneurs choose to hire mobile app developers in India, where adept professionals integrate strong security protocols with economical development.
1. Start With Security-First Architecture
When designing any secure mobile app, it is vital to focus on security at the architectural level. All features, integrations, and workflows within an application must be conceived and constructed around security; “security” cannot be an afterthought, and an application must be constructed to be secured from Day 1 against any type of attack. A good way to ensure the security of your mobile app is to partner with a cost-effective mobile application development company that provides security-first development frameworks.
2. Use Strong Authentication Systems
Passwords alone are no longer sufficient for logging into a mobile application securely. In 2026, Multi-Factor Authentication (MFA), biometric login, and device authorization will be standard methods of authenticating secure applications. By employing these types of Authentication Systems, unauthorized access can be greatly minimized, even if the Login credentials have been compromised. Implementing “Intelligent Logout Session Timeout” will also mitigate reputational risk if a user fails to log out of a shared device. Top-tier, architecture-based security teams at mobile application development companies in India will typically include these authentication methods in their overall security framework.
3. Protect Data Through Encryption
One of the greatest defences you can put in place to protect yourself from threat actors is data encryption, both while “data-at-rest” and “data-in-transit.” Your app should not display your users’ private information, including messages, payments and personal information, unprotected to outside parties.
New encryption protocols protect your data in transit, even when it is captured by a malicious actor. However, if you hire a team of affordable app developers, they will use the most recent version of encryption standards and provide you with a security certificate that will continue to protect your data throughout the entire life of your mobile application.
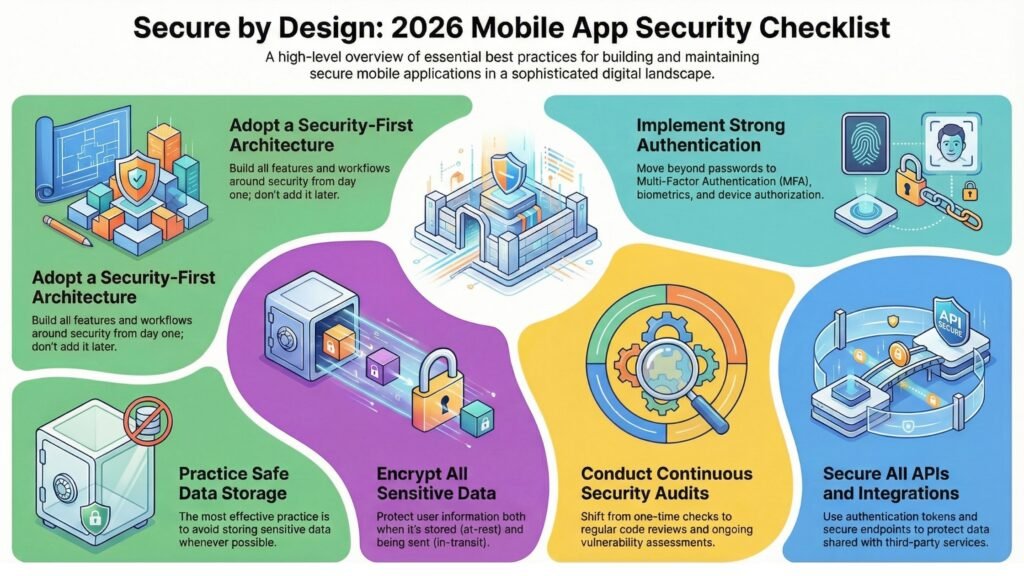
4. Regular Security Audits and Code Reviews
The year 2026 will continue to move away from a model of conducting one-time security checks towards a model of continuous and ongoing security monitoring. Applications will require regular code audits, vulnerability assessments and security assessments that will allow the team that is developing your application to identify vulnerabilities early in the development process and to ensure that future updates of your application do not introduce additional vulnerabilities inadvertently. There are many affordable application development companies available that offer regular and routine application testing and continuous support as part of an extended support program.
5. Secure APIs and Third-Party Integrations
All of today’s modern mobile applications rely heavily on Application Programming Interfaces (APIs). API services include payment processing gateways, mapping services, user authentication services and other forms of integration that improve overall user experience when you use an application. However, many of these APIs can be used by hackers to gain access to your application and/or business if not properly configured and secured. Always make sure to implement authentication tokens and secure endpoints, and allow access to API resources based on permissions.
6. Implement Safe Data Storage Practices
Eliminating the storage of any sensitive data whenever possible is one of the easiest and most effective ways to mitigate the risks associated with securing sensitive information. If you do not need the information, do not keep it. If you are keeping data that you must retain, use secure databases to store your data and encrypt your passwords using a hashing algorithm. This will reduce your exposure in the event of a data breach.
Experienced developers with a mobile app development company in India will follow stringent guidelines concerning how data is handled so that user information is protected properly.
7. Stay Updated With Security Patches
The ability to continually improve application security will depend on protecting your application from being hacked. Developing a partnership with an application development company, such as Boffin Coders, that maintains appropriate equipment and staff for developing your application will provide you with an affordable way to keep your application up-to-date and secure without incurring high costs.
Conclusion
By utilizing strong methods of authentication and encryption, creating a secure architecture, and providing continuous monitoring of your application for security breaches, you can build a product that instills the confidence of your customers while keeping any potential threat at bay.
By developing an affordable app development company or by selecting a trusted mobile app development company in India, you will benefit from having an experienced team that can provide you with affordable ongoing security updates while providing you with a cost-effective solution.